Raymii.org

אֶשָּׂא עֵינַי אֶל־הֶהָרִים מֵאַיִן יָבֹא עֶזְרִֽי׃Home | About | All pages | Cluster Status | RSS Feed
Running TSS/8 on the DEC PiDP-8/i and SIMH
Published: 26-07-2015 | Author: Remy van Elst | Text only version of this article
❗ This post is over ten years old. It may no longer be up to date. Opinions may have changed.
Table of Contents
In this guide I'll show you how run the TSS/8 operating system on the PiDP replica by Oscar Vermeulen, and on SIMH on any other computer. I'll also cover a few basic commands like the editor, user management and system information.
TSS-8 was a little time-sharing operating system released in 1968 and requires a minimum of 12K words of memory and a swapping device; on a 24K word machine, it supports up to 17 users. Each user gets a virtual 4K PDP-8; many of the utilities users ran on these virtual machines were only slightly modified versions of utilities from the Disk Monitor System or paper-tape environments. Internally, TSS-8 consists of RMON, the resident monitor, DMON, the disk monitor (file system), and KMON, the keyboard monitor (command shell). BASIC was well supported, while restricted (4K) versions of FORTRAN D and Algol were available
Introduction
I've recently accuired a PDP-8 remake, the PiDP-8/i by Oscar Vermeulen. This beautiful piece of hand made hardware uses a Raspberry Pi to emulate a PDP-8 with SIMH. The front panel actually works, you can use the switched to load paper tapes, the RIM and BIN loader and all the other legacy goodness. It is a bit smaller than a real PDP-8, it is scale 2:3. The real PDP-8 has 1.5 cm switched, the PiDP-8 has 1.0 cm switches.
I have an interest in legacy systems like the PDP-11, VAX/VMS and other mainframes and minicomputers. The PiDP-8/i allows me to have a small piece of this legacy myself. It also motivated me to learn more about the PDP-8 and it's hard and software. It also inspired me to write this article about it. Since these systems are way older than me, emulation and recreation are the only way for me to use them, sadly.
I really encourage you to check out the PiDP-8. Order one as well, you can either get a kit to construct yourself, or order an assembled version. Support this beautiful piece of work!
SIMH is an emulator which not only emulates a PDP-8, but a lot more older mainframes and minicomputers. See the website for more information about SIMH.
This guide shows you how to run the TSS/8 operating system on the PiDP-8/i remake, and on a regular SIMH emulator. We will use Ubuntu 14.04 as our host operating system, but any OS that runs SIMH will do.
You can see all my PDP-8 related articles here.
The official TSS/8 Users Guide manual can be downloaded online from here, and I've mirrored it on this website as well.
The official Systems Managers guide can be found here and is mirrored on this website here
You can read through the two guides to find out everything on TSS/8, including loading tapes, assembler programming and more. This guide focusses on getting you up and running with TSS/8.
Preparing the PiDP-8/i
If you use the default software with the PiDP-8/i from Oscar you can set the IF switches to octal 1 and toggle the Single Step switch to boot into TSS/8. The IF switches are the leftmost white switches. The DF (Data Field) switches can be used to mount USB sticks as different storage media. The DF switches are the leftmost brown switches. See the image below:
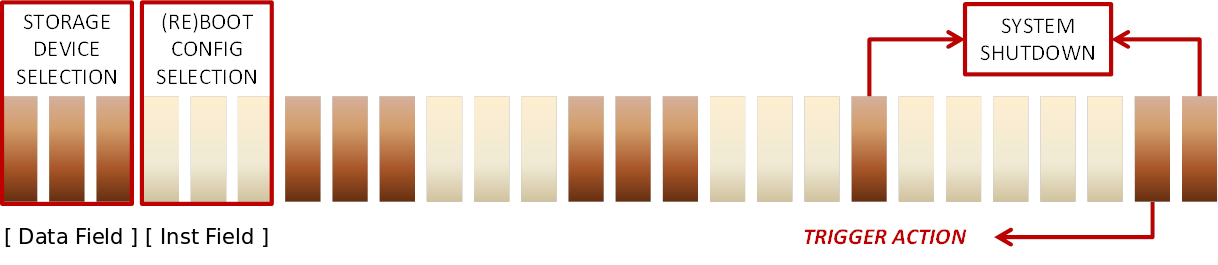
Boot up the PiDP-8/i and hit the middle white switch. Toggle the single step counter, the OS/8 will reboot to TSS/8.
Make sure you are logged in via SSH or the serial console, and connected to the screen session.
If you receive an error message, check the /opt/pidp8/bootscripts/2.script
file. Make sure it is the same as the below SIMH config file.
Installing and configuring SIMH
If you have a PiDP-8/i and want to run from there, skip this section. If you don't and use your regular computer, read on to set up SIMH.
First create a folder where you will store the disk image and the configuration files, and go in that folder:
mkdir pdp8
cd pdp8
Ubuntu, and many other operating systems, have packages available for SIMH. We can use the built in package manager to install simh:
apt-get install simh
If your distro doesn't have simh, see their website for installation instructions.
Download the prepared disk image and loader:
wget https://raymii.org/s/inc/downloads/pdp/tss8_init.bin
wget https://raymii.org/s/inc/downloads/pdp/tss8_rf.dsk
To make the start up proces easier you can set up an 'pdp8.ini' file with a few
commands in it. SIMH will load and run these commands at startup if you execute
the pdp8 command.
Our pdp8.ini file has the following in it:
load tss8_init.bin
set rf enabled
set df disabled
attach rf tss8_rf.dsk
attach ttix 4000
run 24200
It first loads the paper tape bootstrap. It mounts the TSS/8 disk image of the RF08 and it assigns a TCP/IP port to the Telnet listener for the extra terminals. It then runs the bootstrap.
Do note that you don't need to create this file, you can also enter these commands manually at the simh prompt.
In the current folder, execute the following command to start up SIMH with our configuration file:
pdp8
Running TSS/8
If all goes well, you should see something like below on the screen, PiDP-8/i output:
Rebooting /opt/pidp8/bootscripts/2.script
HALT instruction, PC: 20512 (JMP 511)
RX: writing buffer to file
RX: buffering file in memory
Listening on port 4000 (socket 7)
LOAD, DUMP, START, ETC?
Type START followed by ENTER to begin the boot process of TSS/8.
You will be asked for a date and time:
MONTH-DAY-YEAR: mm:dd:yy -- numeric, yy in range [74:85]
HR:MIN - hh:mm -- numeric, 24 hour format
Enter for example 02:24:75 and 22:10. Then type cr to continue to the
login prompt.
Logging in
Login using the following command:
LOGIN USERNAME PASSWORD
The login command does not display or echo.
The list of accounts and passwords in this specific image:
PPN Password
[0,1] VH3M
[0,2] LXHE
[0,3] SHUG
[77,77]
[1,10] WBCN
[20,1] DT
[20,2] PT
[20,3] TSS8
[20,4] EDIT
[20,5] 4TH
[1,50] JERK
We cover more on user management later on in the article, including how to create and modify users.
To login as user 1, the system user enter this:
LOGIN 1 VH3M
To login as user 1,10, (project 1, user 10) enter this:
LOGIN 1,10 WBCN
You will receive the following prompt after logging in:
.
TSS/8.24 JOB 01 [01,10] K00 12:12:36
SYSTEM IS DOWN, INC.
Primitive ls, CAT (catalog)
TSS/8 Monitor maintains a library of disk files for each user. The System Library Program CAT is used to obtain a catalog of the contents of this library. For each file, CAT types the size of the File in units of disk segments. The size of a disk segment may vary among installations. Generally, it is 256 (decimal) words of disk storage. The protection code for the file is also given. (See the section on the PROTECT Monitor command (Chapter 9 of the manual) for a precise explanation of protection codes.) If the program was created by any of the System Library Programs, it has a protection code of l2, meaning that other users can read the File, but only the owner can change it.
When the CAT program is used by the SYSTEM ADMINISTRATOR (user 1), it prints out accounting information. This report consists out of the accumulated time (in hours, minutes and seconds) for central processor usage and connect time as well as the number of disk segments currently being used.
To see the contents of a users library, run the .R CAT:L command. It will ask
for an account number, after which it prints out the users directory. This way
you can trace which user is using an abnormal amount of diskspace.
If you login as the user 2, you can execute the following command to see the contents of the disk:
.R CAT
Output:
DISK FILES FOR USER 0, 2 ON 1-JAN-75
NAME SIZE PROT DATE
PALD .SAV 16 12 31-MAR-76
LOADER.SAV 4 12 31-MAR-76
FORT .SAV 6 12 31-MAR-76
FOSL .SAV 6 12 31-MAR-76
PIP .SAV 10 12 31-MAR-76
TSTLPT.SAV 2 12 31-MAR-76
LOGOUT.SAV 6 12 31-MAR-76
SYSTAT.SAV 5 12 31-MAR-76
EDIT .SAV 8 12 31-MAR-76
FOCAL .SAV 16 12 31-MAR-76
BASIC .SAV 38 12 31-MAR-76
COPY .SAV 10 12 31-MAR-76
CAT .SAV 6 12 31-MAR-76
GRIPE .SAV 5 12 31-MAR-76
LOGID .SAV 4 12 31-MAR-76
PUTR .SAV 21 12 3-FEB-84
ODTHI .SAV 2 12 29-FEB-84
FLAP .SAV 1 12 7-APR-84
PTLOAD.SAV 1 12 29-APR-84
BLANK .SAV 1 12 9-JUN-84
DTTEST.SAV 2 12 26-JUN-84
INIT .SAV 17 12 29-JUL-84
BAS000.TMP 1 17 1-JAN-84
BAS100.TMP 1 17 1-JAN-84
INTER .BAS 1 12 1-JAN-75
REMY .ASC 1 12 1-JAN-75
TOTAL DISK SEGMENTS: 189 QUOTA: 1575
System Status
With the SYSTAT command you get a full printout of what the system is doing,
who is logged in and more:
SYSTAT
STATUS OF TSS/8.24 DEC PDP-8 #1 AT 12:19:14 ON 1 JAN 75
UPTIME 00:07:14
JOB WHO WHERE WHAT STATUS RUNTIME
1 0, 2 K00 FOCAL ^BS ^Q 00:00:01
2 1,50 K01 SYSTAT RUN ^Q 00:00:00
AVAILABLE CORE 16K FREE CORE=312
BUSY DEVICES NONE
103 FREE DISK SEGMENTS
There are two users logged in, user 2 on teletype 0, user 50 on teletype 1. User
2 is was FOCAL but is now on the prompt (STATUS ^BS means monitor mode, that
is the prompt), user 50 is executing the SYSTAT command.
The manual has more information on SYSTAT, listed here for convinience.
It is frequently useful to know the status of the system as a whole; how many users are online, where they are, what they are doing, etc. The SYSTAT program provides this capability.
SYSTAT responds by printing on the first line: the version of the TSS/8 Monitor being run, the time, and the date. SYSTAT reports the uptime which is the length of time in hours, minutes, and seconds since the system was last put online.
SYSTAT lists all online users. Each user is identified by his account number. The job number assigned to him and the number of the console he is using are indicated, as is the particular System Program he is running. The exact running state of each user, whether he is actually running (RUN), typing in (KEY) or out (TTY), doing input/output on another system device (IO or FIP), or not running (iB), is indicated.
The amount of computer time used by each user since he logged in is given.
It more users are online than the system has core Fields to hold them, the Fact that the system is swapping is reported. The number of Free core blocks used internally by TSS/8 Monitor for Teletype buffering and various other purposes is typed out.
Then SYSTAT reports any unavailable devices, i.e. , devices which are assigned to individual users. The job to which they are attached and their status (AS if they are assigned but not active, AS+INIT if they are assigned and active) is also indicated.
Finally, the number of available segments of disk storage is reported.
To see the time that you have been logged in:
.TIME
00:00:20
To see the system time:
.TIME 0
12:20:44
FOCAL69
You can start up the FOCAL69 programming environment with the R FOCAL command,
output below:
.R FOCAL
SHALL I RETAIN LOG, EXP, ATN ?:NO
SHALL I RETAIN SINE, COSINE ?:NO
PROCEED.
*_TYPE "HELLO WORLD"
HELLO WORLD*
To exit FOCAL, press CTRL+B followed by the S. Your prompt will be back to a
dot (.):
*^BS
.
Chatting
You can use the TALK command to talk to other users logged in. Fire up TELNET
on port 4000 on a terminal or two and login with the users 2, and 1,50
(password JERK). On the 1,50 terminal, enter the following command to talk to
the system administrator (on teletype 0):
.TALK 0 PLEASE HELP
On the 2 telnet session you will see this:
** K01 [01,50] **
PLEASE HELP
You can talk back:
.TALK 1 WHATS UP DOG
Telnet 1,50 will see this:
** K00 [00,02] **
WHATS UP DOG
As the system administror (user 1) you can also send a message to all users at
one with the BROADCAST command. The following command:
.BROADCAST THE SYSTEM WILL SHTUDOWN IN 5 MINUTES
Will result in the following messages on all terminals (they are interupted):
*** THE SYSTEM WILL SHTUDOWN IN 5 MINUTES
BASIC-8
TSS/8 has a BASIC programming environment. Start it up with the R BASIC
command. It will ask you if you want to create a NEW file or load an OLD one.
Here's an example program, from the TSS/8 manual, to calculate loan interest. We
first enter a line number, then the instruction. Afterwards we save the file as
INTER.BAS with the SAVE command. We then run the script with the RUN
command.
.R BASIC
NEW OR OLD--NEW
NEW PROGRAM NAME--INTER
READY
10 REM - PROGRAM TO COMPUTE INTEREST ON A LOAD
20 PRINT "INTEREST IN PERCENT";
30 INPUT J
40 LET J=J/100
50 PRINT "AMOUNT OF LOAN";
60 INPUT A
70 PRINT "NUMBER OF YEARS";
80 INPUT N
90 print "NUMBER OF PAYMENTS PER YEAR";
100 INPUT M
110 LET N=N*M
120 LET I=J/M
130 LET B=1+I
140 LET R = A*I/(1-1/B^N)
150 PRINT "MONTHLY PAYMENT ="R
160 PRINT "TOTAL INTEREST ="R*N-A
170 END
SAVE INTER
RUN
Output:
INTEREST IN PERCENT? 8
AMOUNT OF LOAN? 25000
NUMBER OF YEARS? 20
NUMBER OF PAYMENTS PER YEAR? 12
MONTHLY PAYMENT = 209.1103
TOTAL INTEREST = 25186.46
READY
Exit BASIC with the BYE command.
EDIT, the line editor
TSS/8 Editor provides the user with a powerful tool for creating and modifying source files on-line. EDIT allows the user to insert, change and append lines of text; and then obtain a clean listing of the updated file. EDIT also contains commands for searching the file for a given character.
- Page 56, 6-1, DEC TSS/8 User guide
EDIT considers a file to be divided into logical units, called pages. A page of text is geranlly 50-60 lines long, and hence corresponds to a physical page of program listing. A FORTRAN-D program is generally 1-3 pages in length; a program prepared for PAL-D (the assembler) may be several pages in length. EDIT operates on one page of text at a time, allowing the user to relate his editing to the physical pages of his listing. EDIT reads a page of text from the input file into its internal buffer where the page becomes available for editing. When a page has been completely updated, it is written onto the output file and the next page of input is made available. EDIT provides several powerful commands for "paging" through the source file quickly and conveniently.
The end of a page of text is marked by a form feed (CTRL+L) character. Form
feed is ignored by all TSS/8 language processors.
Here is the EDIT Command summary table from the manual.
Command | Format(s) | Meaning
---|---|---
READ | R | Read text from the input file and append to buffer until a formfeed
is encountered.
APPEND | A | Append incoming text from keyboard to any already in buffer untila
form feed is encountered.
LIST | L
nL
m,nL | List the entire buffer.
List line n.
List lines m through n inclusive.
PROCEED | P
nP
n,mP | Output the contents of the buffer to the output file, followed by a form
feed.
Output line n, followed by a form feed.
Output lines m through n inclusive followed by a form feed.
TERMINATE | T | Close out the output file and return to TSS/8 Monitor.
NEXT | N
nN | Output the entire buffer and a form feed, kill the buffer and read the next
page.
Repeat the above sequence n times.
KILL | nD
n,mD | Delete line n of the text.
Delete lines m through n inclusive.
INSERT | I
nI | Insert before line 1 all the text from the keyboarduntil a form feed is
entered.
Insert before line n until a form feed is entered.
CHANGE | nC
m,nC | Delete line n, replace it with any number of lines from the keyboard
until a form feed is entered.
Delete lines m through n, replace from keyboard as above until form feed is
entered.
MOVE | m,n$kM | Move lines m through n inclusive to before line k.
GET | G | Get and list the next line beginning with a tag.
SEARCH | S
nS
m,nS | Search the entire buffer for the character specified (but not echoed)
after the carriage return. Allow modification when found. TSS/8Editor outputs a
slash (/) before beginning a SEARCH.
Search line n, as above, allow modification.
Search lines m through n inclusive, allow modification.
END | E | Output the contents of the buffer. Read in any pages remaining in the
input file, outputting them to the output file. When everythingin the input file
has been moved to the output file, close it out and retum to the TSS/8 Monitor.
E is equivalent to a sufficient number of N's followed by a T command.
^C | CTRL+C | Stop listing and return to Command Mode.
You can download the two pages from the manual PDF as well from here.
Using the I command you can enter text, with a CTRL+L you exit insert mode.
Save your file with E.
User management
Above in the article there was a list of users for this image. Here below we cover the users, projects and permissions in more detail.
The account number is actually two numbers, a project number and a programmer number. Account number 5440 is project number 54 and programmer number 40. Account number 102 is project 1, programmer 2. For this reason, account numbers may be specified as two numbers seperated by comma's (i.e. 1,2), as wel as a single number (102). Users may specify that all other user may share their files, only users whose project number is the same, or no users at all.
The library account number (2 or 0,2) is no different from any other account number. Users logged in as account number 2 may use TSS/8 just as any other user would. The one thing that makes it special is that the R command automatically fetches the specified program from the library of account number 2. In this way users may get programs from this library without knowing specifically its account number. The reason the library password is kept secret is to prevent users other than the system manager from altering its contents.
The system account number (1 or 0,1) is privileged. When logged in with this account number and, password, the user has access to several unique capabilities, such as defining new passwords. It is, therefore, quite important that the system password remain secret.
LOGID is the program used to create new account number, password combinations.
It is only usable by a user logged in with the system password. Therefore, the
next step in the system building process is to log in with this password (the
account number is 1).
LOGID is then called by typing:
.R LOGID
LOGID prints opening instructions, then an asterisk, and waits for you to specify the user's account number and password separated by a space. As usual, terminate the line with the RETURN key. After entering the combination, LOGID prints an asterisk and waits for another user account number-password combination.
When all desired users and passwords have been defined, type CTRL+B and then
S. Complete the process by logging out with the LOGOUT command followed by
RETURN.
To delete (close) a user, open the LOGID program like above, and enter the
username and password (can be any password), followed by the ESC key (ALT
mode). The account number and all the files will be deleted, LOGID will print
DELETED and another asterisk.
Conclusion
This concludes my overview of TSS/8. You are now able to edit files and users, gather some system information and run BASIC programs. This should get you started with the system and allow you to explore it more yourself.
The two manuals cover way more on the system, like a full assembler, FORTRAN and BASIC programming guide, and all aspects of interacting with peripherals like disks, tape readers and teletypes. They both are quite an interesting read.
Tags: adventure , articles , dec , fortran , os-8 , pdp , pdp-8 , pidp8 , simh , tss-8